How charities can achieve greater resilience with cybersecurity
Digital security and privacy compliance are becoming more and more important for charities today. Cyber threats have never been so prevalent and data privacy issues are increasingly complex. In the past, cybersecurity and privacy were often low on the priority list for charities —but times are changing. According to a Government report, a fifth of UK charities identified cybersecurity breaches or attacks in 2018. The stakes are high as breaches, compromised data and cyberattacks can put vulnerable beneficiaries at risk, disrupt operations and services, expose organisations to liability and tarnish the reputation charities have so painstakingly built.
So, what can charities do to achieve greater cybersecurity resilience?
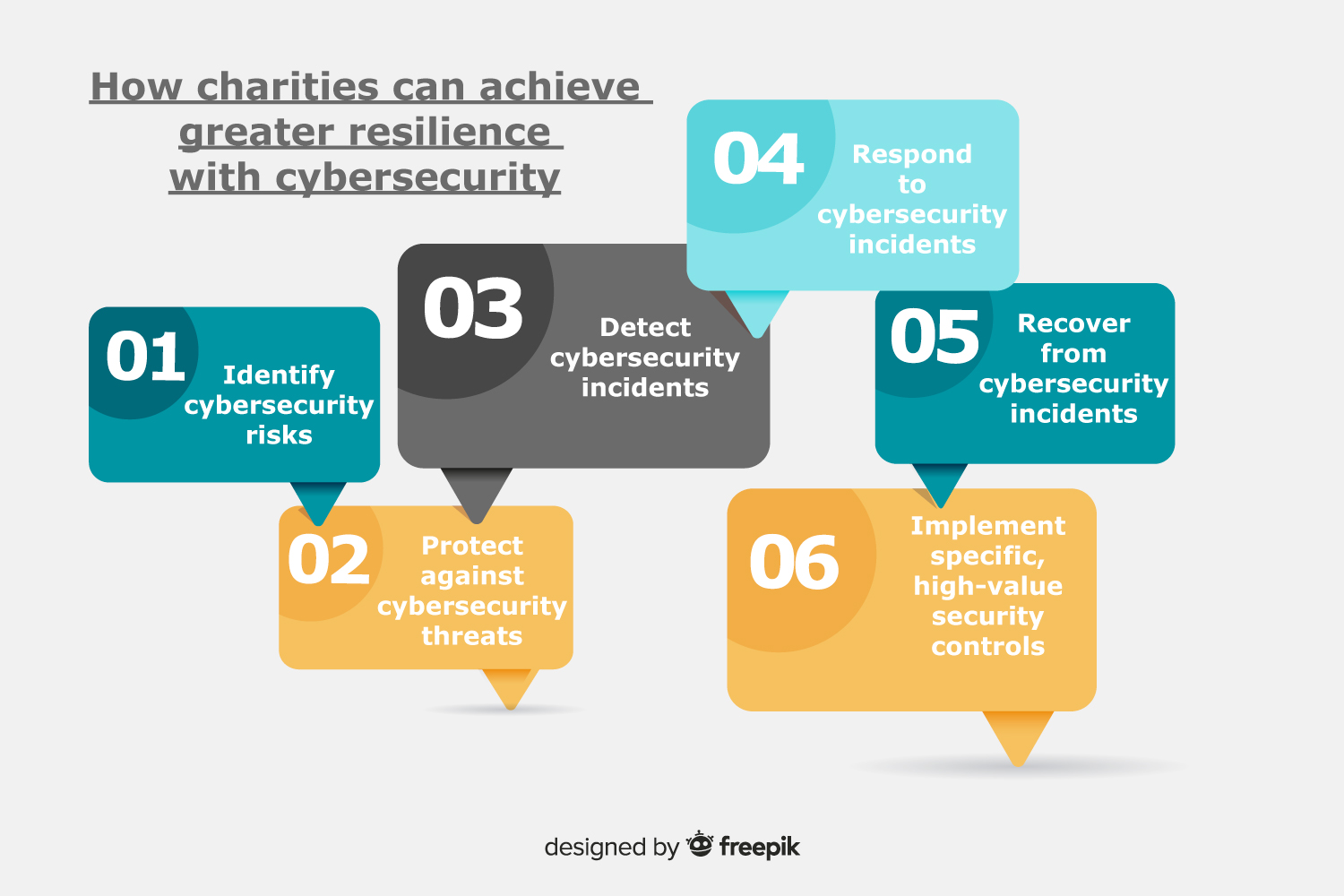
As a great starting point, charities can focus on the following six goals:
- Identify cybersecurity risks
Charities need to develop an understanding of the cybersecurity risks confronting their organisation, including the risks to systems, assets, data and capabilities. By doing so it will allow the organisation to better manage risks by focusing and prioritising its cybersecurity efforts in a manner consistent with the organisation’s risk management strategy and business needs.
- Protect against cybersecurity threats
Another element charities can look at is to develop safeguards to protect against cybersecurity threats by implementing practices that will help limit or contain the impact of a cybersecurity event.
For instance:
- Establish access control procedures to limit individual access to what employees need to perform their jobs, adjust it when they change positions and immediately revoke access when a staff member leaves the organisation.
- Conduct training for staff and partners to ensure all users are informed and trained on cybersecurity awareness. This can include ensuring users develop an understanding of cybersecurity threats to them and the devices they use; how to recognise common types of cybersecurity attacks (e.g. phishing); and how to report a suspected cybersecurity incident.
- Establish data security practices, which can help mitigate the impact of any potential cybersecurity incident or data breach.
- Ensure cybersecurity is considered when implementing information security policies, maintenance and repair procedures and any technical security solutions (e.g. by maintaining and reviewing audit records).
- Detect cybersecurity incidents
Cybersecurity incidents are often difficult to detect. Microsoft security research has shown on average, attackers spend 146 days (20+ weeks) on a network before detection. However, implementing certain processes and monitoring solutions makes it much easier to timely detect anomalies or security events impacting the organisation’s information systems.
- Respond to cybersecurity incidents
Once a cybersecurity incident is detected, the organisation needs to have a plan in place to efficiently and effectively respond to and contain the impact of an incident. Important components of cybersecurity incident response are:
- Planning for the incident response, including developing and testing an incident response plan.
- Coordinating incident response activities between internal and external stakeholders.
- Conducting analysis to ensure the organisation adequately responds to the cybersecurity incident. This analysis can also help support recovery by providing more detail about what occurred during the cybersecurity incident.
- Containing and mitigating an existing cybersecurity incident, including analysing the circumstances or vulnerabilities that led to the incident to mitigate the risk of future incidents.
- Improve the organisation’s incident response activities based on lessons learned from the cybersecurity incident.
- Recover from a cybersecurity incident
After a cybersecurity incident is over, the organisation needs to recover and resume normal operations. Although full recovery can take time, being prepared before an incident happens makes it easier for an organisation to restore any capabilities or services that were impaired or lost and reduce the impact of a cybersecurity event. Charities should consider developing procedures to execute recovery plans; ensure sufficient backup capabilities exist; update recovery plans based on lessons learned from the cybersecurity incident; and coordinate with internal and external stakeholders to safely and securely restore normal operations.
- Implement specific, high-value security controls
While charitable organisations move towards strengthening their digital security strategies, charities can implement a subset of identified security controls as soon as practicable.
- Create backups of all data regularly to reduce the risk of data loss after a natural disaster or cyberattack.
- Update software and hardware regularly to manage the product lifecycle of hardware and software.
- Implement multifactor authentication to provide greater security when users are accessing the organisation’s network.
- Use virtual private networks for remote access to provide greater security when users are accessing the organisation’s network remotely.
- Enable endpoint protection to provide greater protection to the organisation’s devices. Endpoint protection can monitor users’ devices to help identify threats—such as phishing links—and block them so that the network is not exposed.
- Monitor devices to provide additional protection to the organisation’s devices.
- Restrict usage of personal mobile devices to reduce the number of devices an attacker could attempt to exploit to gain access to the organisation’s network.
Whilst it is important for charities to move ahead with their digital transformations, ensuring they remain “cyber secure” should be a fundamental consideration. Fundraising and finance systems like those supplied by Microsoft come with a wealth of benefits including the comfort of being supported by an organisation that takes security extremely seriously. Microsoft has invested over $1bn USD into security research and development, plus it has 3,500 cybersecurity experts working with them. Dynamics 365 itself has multi-layered, built-in security controls that safeguard data and streamline compliance. If you would like to understand more about our NfP 365 suite of solutions that have been built on Microsoft Dynamics 365 and tailored to the charity sector, then feel free to contact us today.
Jenny Tomlinson
Marketing Manager
